| assets | ||
| client | ||
| docker | ||
| dvwa | ||
| server | ||
| server-ml | ||
| sqlmap | ||
| suricata | ||
| .gitignore | ||
| .prettierrc | ||
| .tool-versions | ||
| README.md | ||
CSPJ Application
HOW TO TEST
The IP address refers to the IP address that y'all configure for the VM.
1. DVWA (ignore)
DVWA is listening on port 80, so in the browser no need to enter port number.
Just navigate to the IP address.
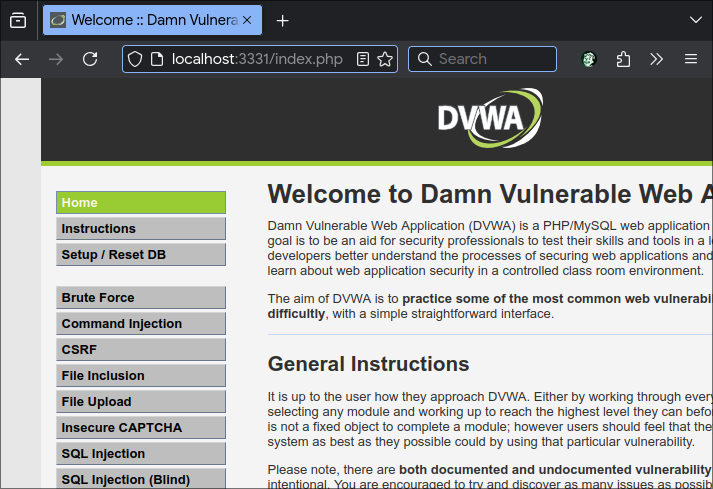
2. ModSecurity DVWA
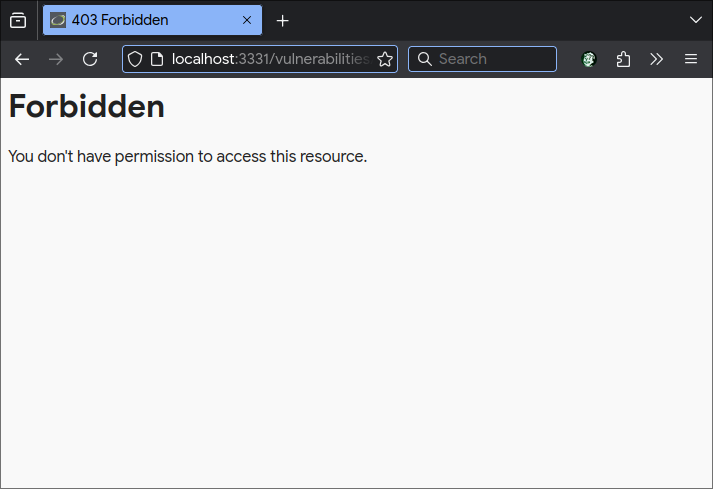
ModSecurity is listening on port 3331, it is a proxy for DVWA.
Go to <ip>:3331 in the browser.
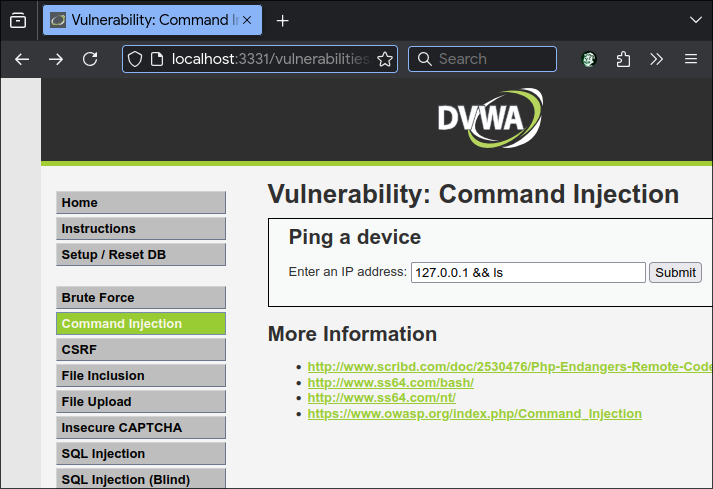
Go to the Command Injection tab.
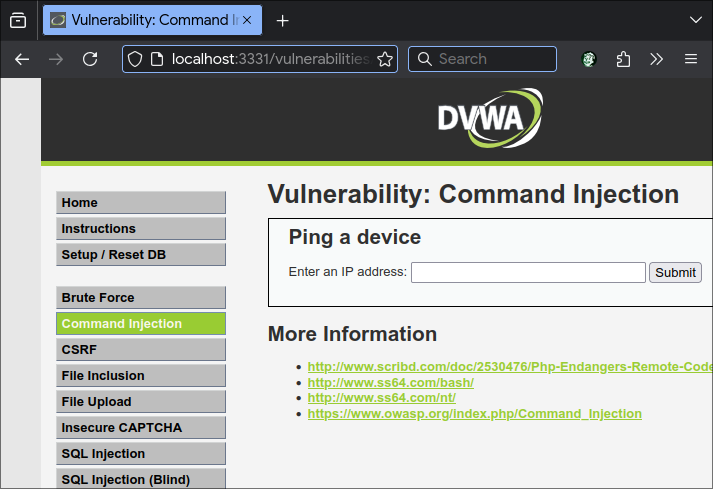
If 401 Forbidden error is returned, ModSecurity is great success.
3. Client + Backend Server + ML Model (ignore)
Start the cspj-application program, be it on Windows or Linux.
Backend server is listening on port 3333.
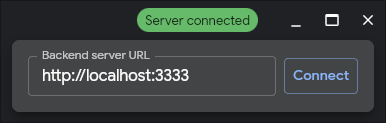
At the top right of the program window, click on the red Server disconnected thingy.
Enter the IP address, and make sure port is set to 3333.
Click connect, and it should turn green.
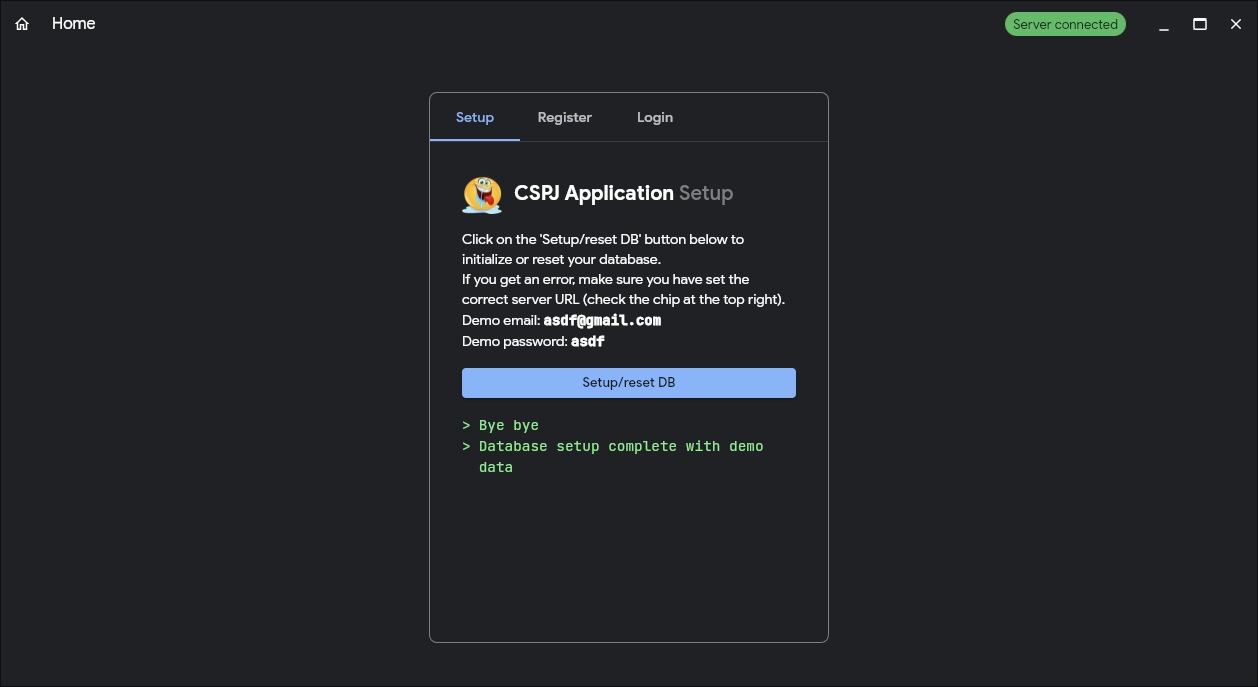
Press the humongous blue Setup/reset DB button.
Should see that DB setup was carried out.
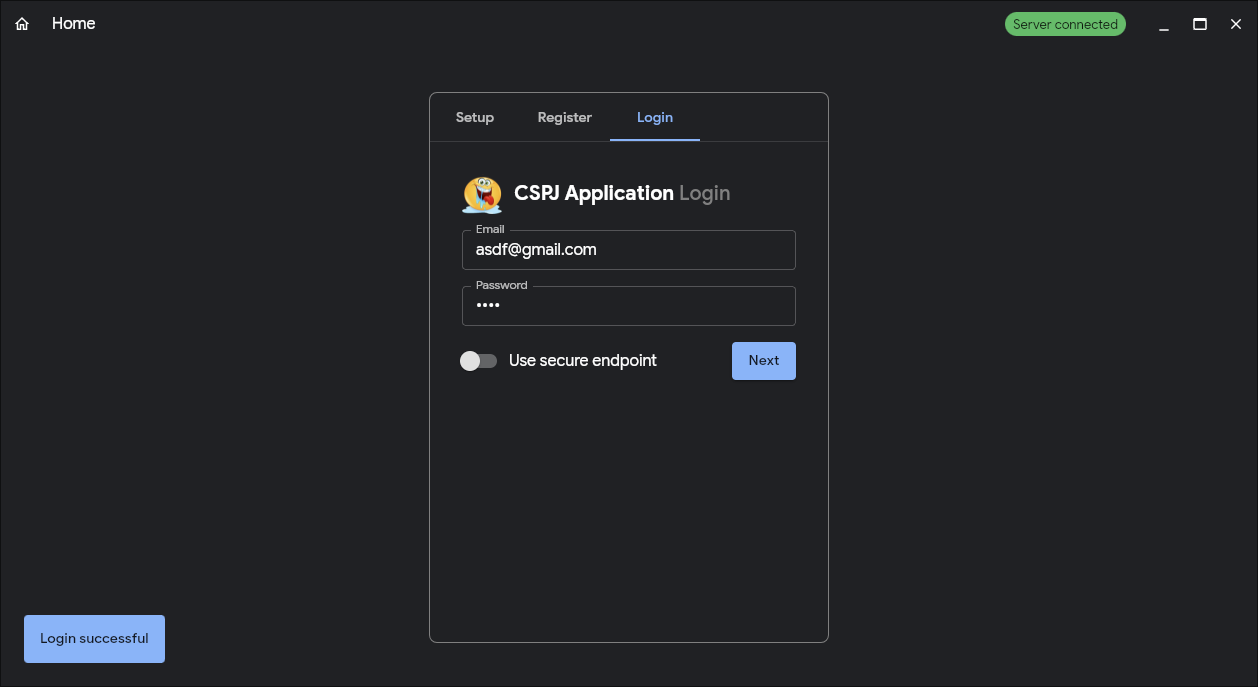
Go to the Login tab.
Enter:
- Email:
asdf@gmail.com - Password:
asdf
Press next, and should see Login successful.
Turn on the secure endpoint switch.
Enter:
- Email:
asdf@gmail.com' OR 1=1; -- - Password:
randompasswordjakfl;dsjflkadsjlkf;sjkfl;dj;l
Press next again.
This time should fail.
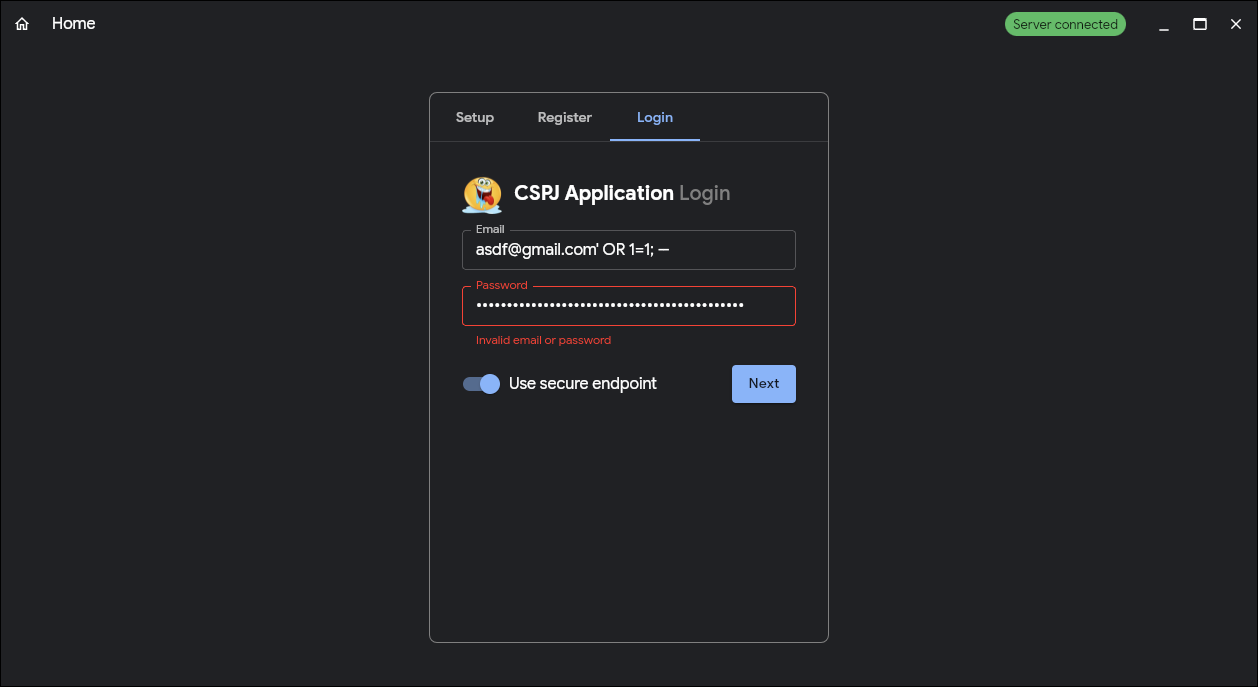
Okay done.
Everything below can ignore
Setup
Requirements
User to be added into docker group.
sudo usermod -aG docker $USER
Services
- 3331: Apache + ModSecurity
- 3332: Suricata
- 3333: Backend server
- 3334: Python backend server
- 3335: PostgreSQL
- PostgreSQL
Python ML server- Backend server
Suricata- Apache + ModSecurity
- Client
Presentation Flow
- [video] start postgres: postgres docker compose -> start pg docker
- [video] start backend: show main.go -> http.go -> db.go -> go build . -> ./server
- [video] setup db: postman -> /nuke-db -> /setup-demo-db
- skip account registration
- [video] login account normally -> show normal login
- [video] do sql injection on unsecure endpoint -> show success
- [video] do sql injection on secure endpoint -> show unsuccess
- [slides] show backend code, unsecure login endpoint -> show concatenation of sql query
- [slides] show backend code, secure login endpoint -> parameterization of sql query
- [video] start apache reverse proxy + modsecurity: docker compose file -> start docker
- [video] change server url on client to reverse proxy -> do sql injection -> show rejection
- [video] zaproxy scan endpoint: start zaproxy -> send first request to unsecure server endpoint with arguments -> include context -> start attack -> show breached
Content-Type: application/json- same as on top
- [video] zaproxy scan reverse proxy: send first request to unsecure reverse proxy endpoint with argumens -> include context -> start attack -> show unbreached
Server
!only listening on localhost is supported. DO NOT run this on a public ip.
/health/health-db/setup-demo-db/nuke-db/fetch-all-users
SQL Injection
Use ' OR 1=1; --
Use tohyouxuan@gmail.com' UNION SELECT id, email, password FROM users WHERE email = 'tohyouxuan@gmail.com'; --
/unsecure-register-sql/secure-register-sql/unsecure-login-sql/secure-login-sql
1. Parameterization of Queries
Used pool.Query() with a parameterized query, instead of dynamically constructing the SQL query by directly inserting the user input.
Parameterized queries separate the SQL code from the data, so user input is never directly put into the query's structure. Placeholders are used instead, and the data is passed as parameters. The DB will treat them as data, not executable code.
ZAP
Content-Type: application/json
{
"email": "tohyouxuan@gmail.com",
"password": "testpassword"
}